Branchen- und regulatorische Risiken
Absicherung gegen Audits und Compliancerisiken
Angesichts zunehmender IT-Sicherheitsvorgaben, externer Bedrohungen und Audits von Softwareherstellern können Unternehmen es sich nicht leisten, sich bei der Überwachung von IT-Assets zurückzulehnen. Sie können Ihre Compliance proaktiv stärken, indem Sie Anschaffung, Lizenzen und Nutzung von Software sorgfältig dokumentieren und Lifecycle-Management betreiben, etwa durch rechtzeitiges Patchen kritischer Schwachstellen. Flexera liefert Ihnen die nötigen aktuellen Daten, damit Sie Ihre Compliance nachweisen und rechtliche und finanzielle Konsequenzen vermeiden können.
Empfohlene Produkte
Optimale Ausrichtung auf komplexere Vorschriften und Risiken
Complex regulatory landscape
Mühelose Einhaltung von Vorschriften
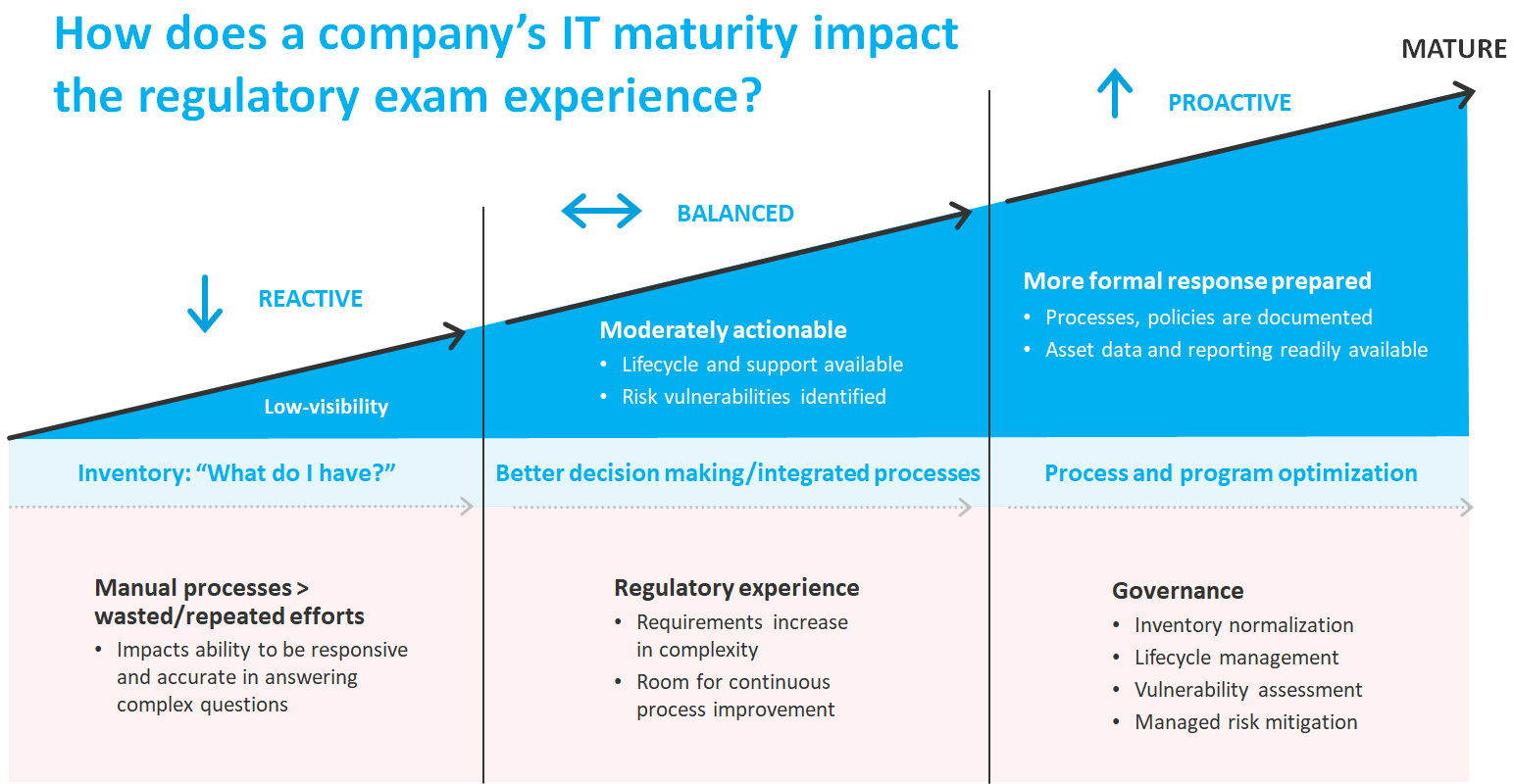
Unternehmen sind mit einer unglaublichen Menge an Vorschriften und Standards konfrontiert, bei deren Nichteinhaltung empfindliche Strafzahlungen drohen. Ob es um den Schutz von Investitionen und Daten der Benutzer geht, um die Festlegung von Sicherheitsrichtlinien oder um die Vermeidung oder Eindämmung von Risiken – die Compliance kann angesichts des strengen regulatorischen Umfelds unmöglich erscheinen. Mit Flexera können Sie allen Anforderungen gerecht werden und Risiken durch Sicherheitslücken zuverlässig identifizieren und verringern. Ermitteln Sie Geräte mit Sicherheitsmängeln, kategorisieren Sie sie nach deren Schweregrad, und erhalten Sie Einblicke in wirksame Schutzmaßnahmen für Ihre Umgebung.
Growing cybersecurity risks
Rechtzeitige Anwendung von Softwarepatches
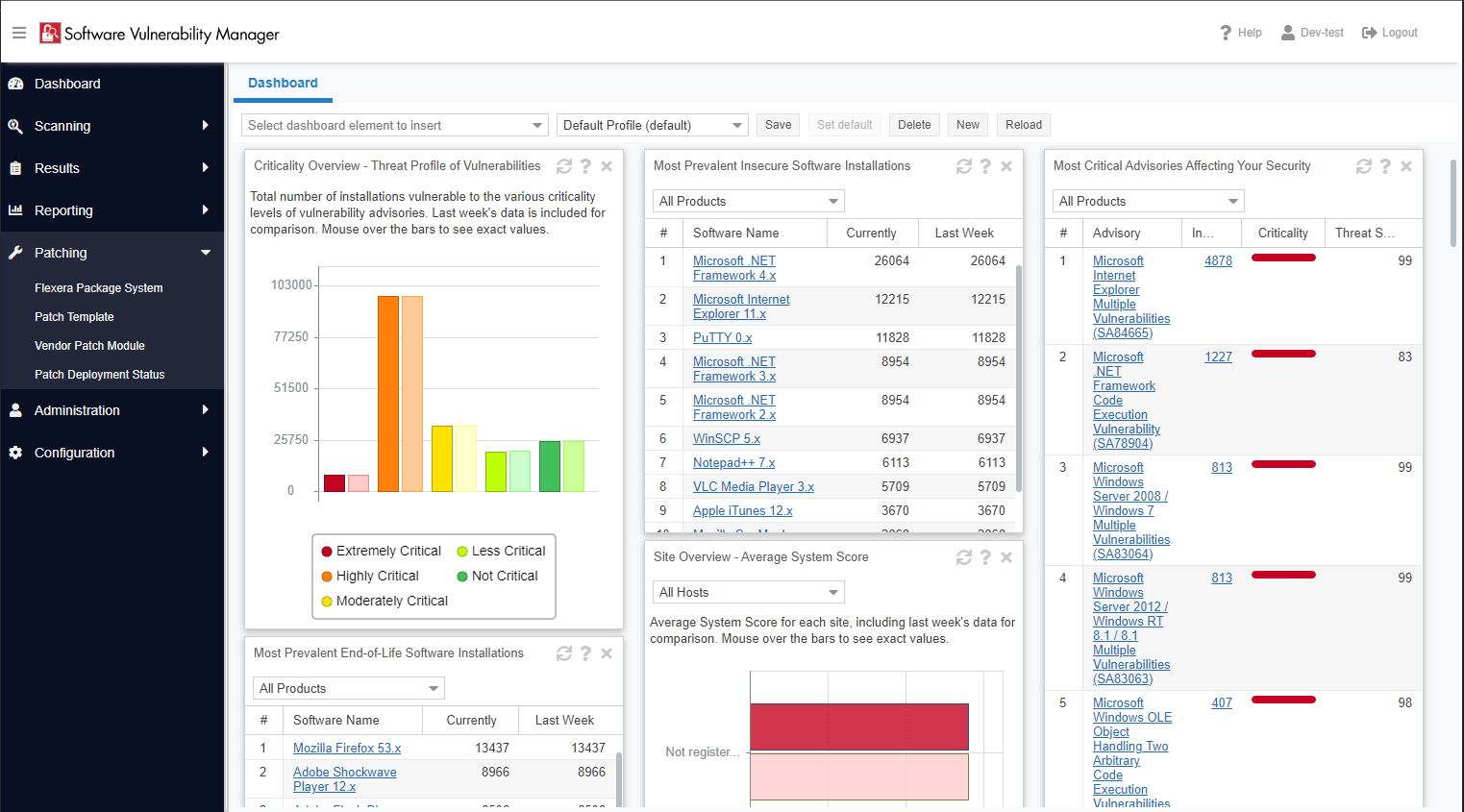
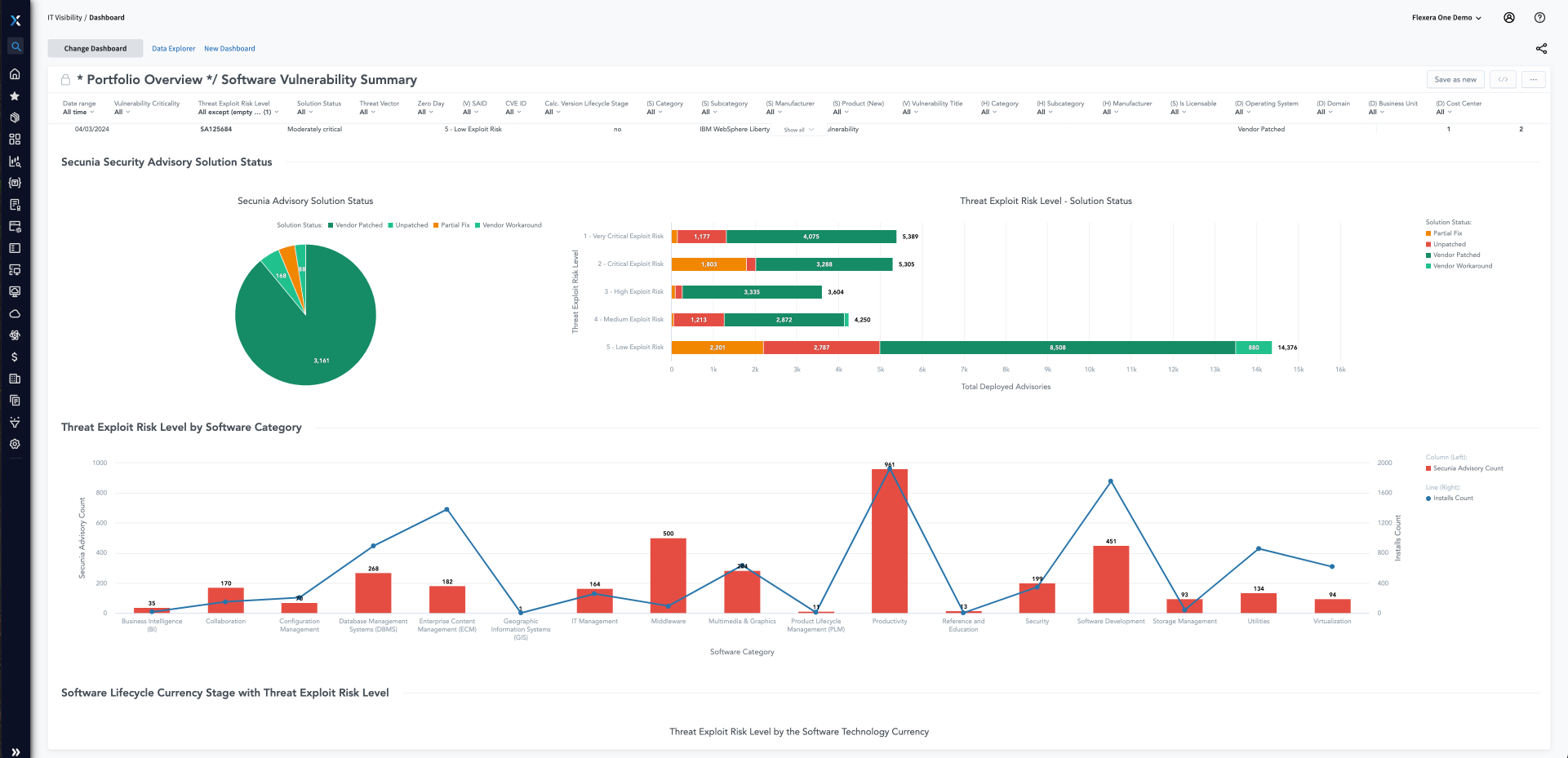
Cybersicherheitsvorfälle reichen von Datenschutzverletzungen, bei denen Millionen von vertraulichen Daten offengelegt werden, bis hin zu ausgeklügelten Ransomwareangriffen, die kritische Infrastrukturen lahmlegen. Cyberkriminelle verfügen mittlerweile über die nötigen Tools, um Zero-Day-Schwachstellen innerhalb weniger Stunden aufzuspüren. Bleiben Sie Angreifern einen Schritt voraus, und sichern Sie Ihre Umgebungen ab, indem Sie mit den branchenführenden Advisories von Secunia Research und Tools zum Management von Softwareschwachstellen Patches identifizieren, priorisieren und installieren.
Simplify complex regulatory challenges
Erkennung und Verwaltung von Risiken
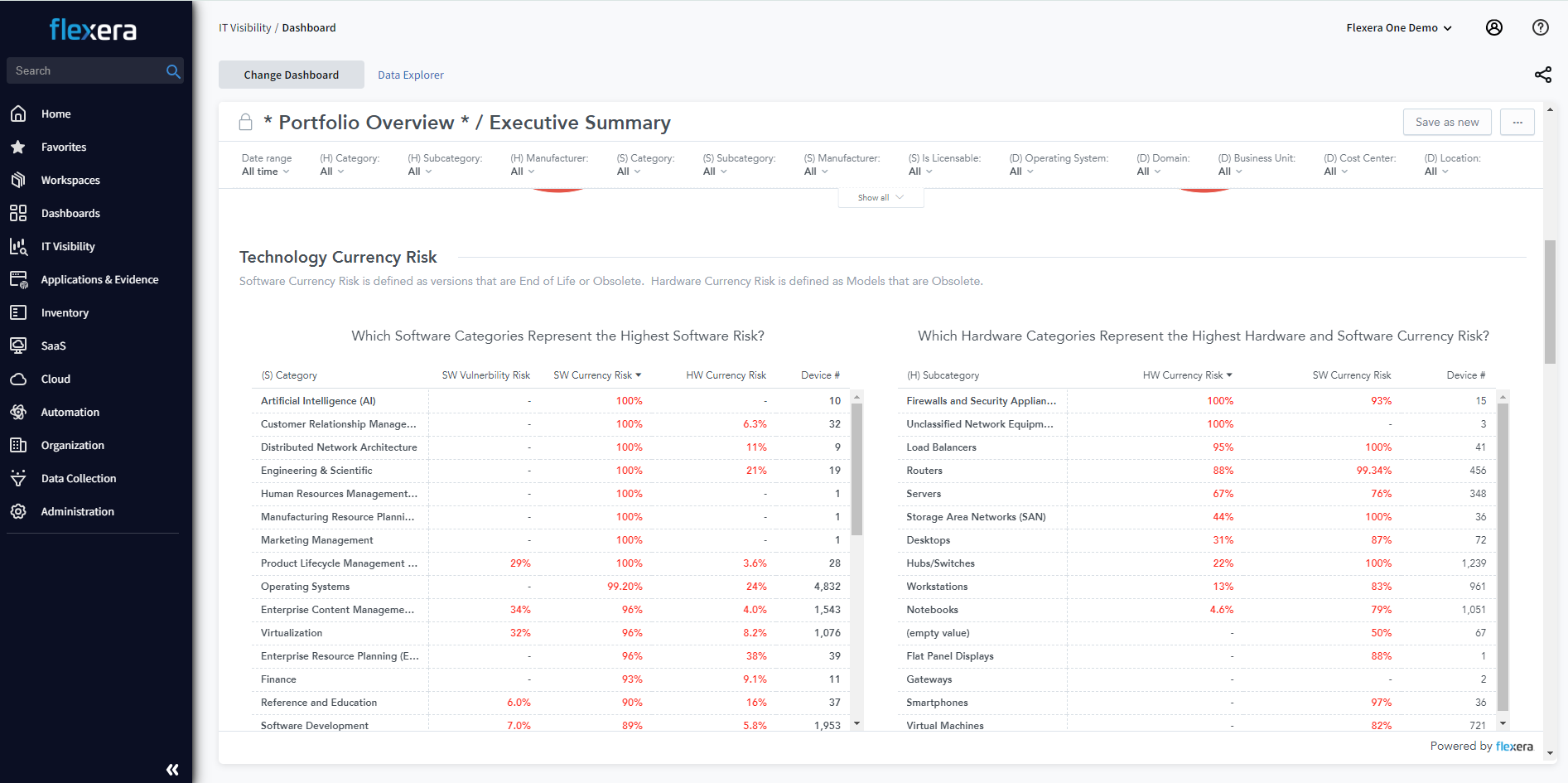
Streng regulierte Branchenumgebungen mit ihren finanz-, gesundheits-, bildungs- und technologiebezogenen Vorschriften können IT-Experten das Leben schwer machen. Um diesen Anforderungen gerecht zu werden, braucht es einen umfassenden Überblick über Assets, die sich dem EOL nähern, und ein entsprechendes Verständnis der damit verbundenen Auswirkungen, die im Hinblick auf branchenspezifische Bestimmungen zu erwarten sind.
Remediate software vulnerabilities
Identifizierung und Priorisierung von Risiken
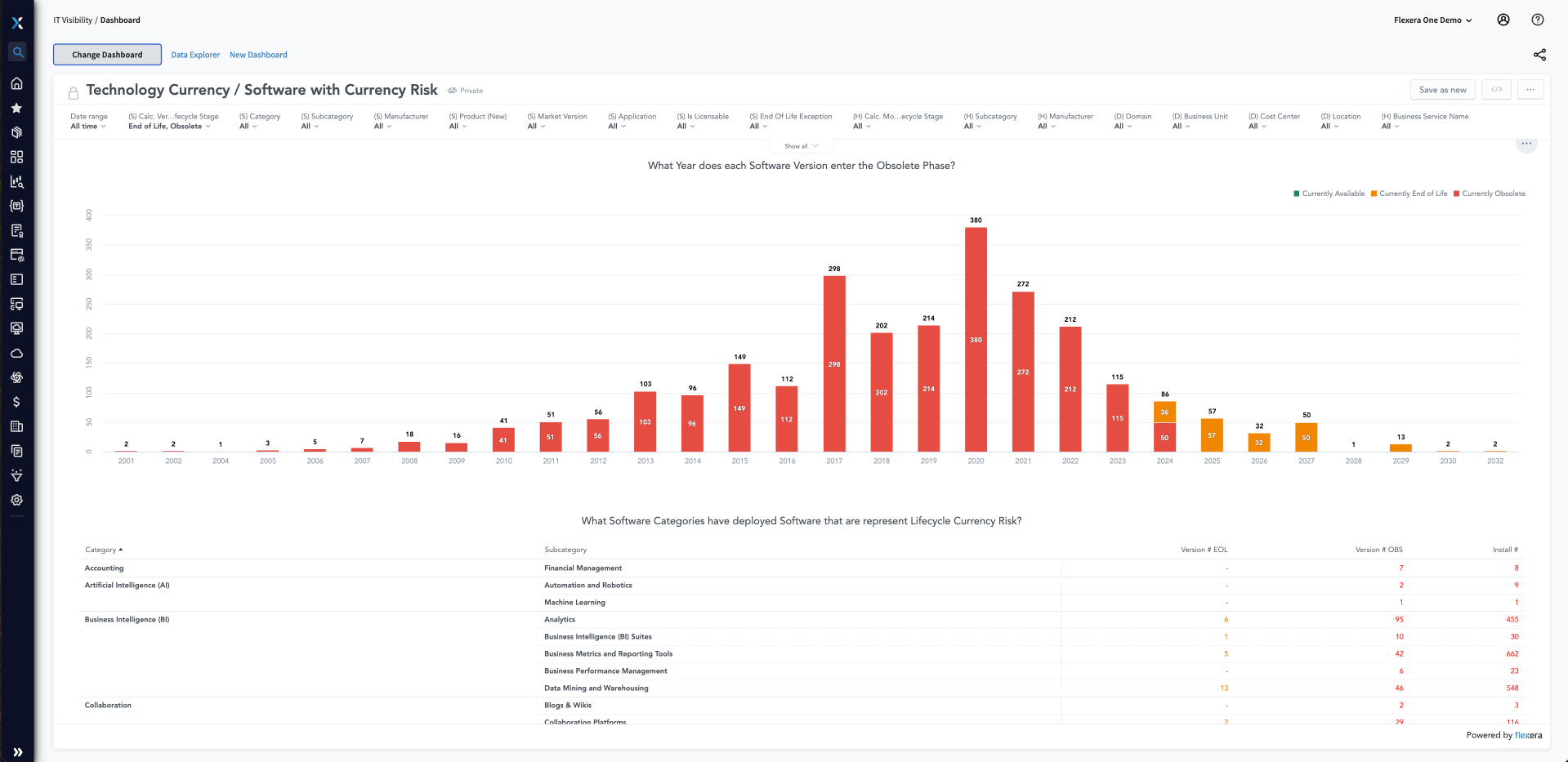
Erkennen Sie anfällige Anwendungen in Ihrem aktiven Bestand, und ermitteln Sie deren Angriffsvektoren. Flexera bietet Ihnen Zugriff auf aussagekräftige Daten von Secunia Research, damit Sie bestens aufgestellt sind, um IT-Risiken zu erkennen und Ihr Unternehmen zu schützen. Nach erfolgreicher Risikoerkennung stellt Flexera Ihnen wertvolle Kontextdaten (einschließlich EOS/EOL, Abteilung und Standort) zur Priorisierung von Behebungsmaßnahmen zur Verfügung.
„Der [Software Vulnerability Manager] hat uns geholfen, die Sicherheitsprobleme des Produkts zu ermitteln. So konnten wir Vorkehrungen zum Umgang mit diesen Bedrohungen treffen. Die Aufspaltung der Anwendung und Implementierung von Microservices unter Einbindung des Vulnerability Manager führte zu einer effizienten Produktarchitektur.“
Häufig gestellte Fragen (FAQs)
EOS steht für End-of-Support und bezeichnet das Datum, ab dem für ein Softwareasset keine weiteren Patches, Updates oder Fixes mehr bereitgestellt werden. Das ist enorm wichtig, denn in der Software vorhandene Exploits werden erkannt. Ohne den Schutz durch aktuelle Patches wird Software anfällig für Bedrohungen, sodass Cyberkriminelle auf die vertraulichen Systeme eines Unternehmens zugreifen können. Flexera hilft Ihnen, diese EOS-Assets schnell zu erkennen, damit Sie die erforderlichen Updates planen können.
EOS-Software und -Geräte sind beliebte Angriffspunkte für Cyberkriminelle. Daher machen Aufsichtsbehörden die Einführung neuerer Versionen zur Auflage, wenn Unternehmen Compliance erreichen und wahren wollen. Wenn Sie in einer regulierten Branche wie Finanzdienstleistungen, Gesundheitswesen oder Bildung tätig sind, kann der Einsatz von EOS-Assets schnell dazu führen, dass Sie gegen Compliancevorgaben verstoßen. Das kann ein behördliches Audit zur Folge haben oder sogar einen Sicherheitsvorfall. Vermeiden Sie solche Situationen, und nutzen Sie Lösungen von Flexera für das Management von Softwareschwachstellen.
Das Team von Secunia Research wird bei Flexera sehr geschätzt. Es stellt genaue und vertrauenswürdige Daten zu Schwachstellen bereit. Heute ist es wichtiger denn je, für Schwachstellendaten den Einsatz von Drittanbietern wie Secunia Research in Erwägung zu ziehen, denn die aktuelle NVD-Datenbank ist veraltet. Das Team setzt sich aus mehreren Sicherheitsexperten zusammen, die in der Branche große Anerkennung genießen. Einige unserer Teammitglieder wurden sogar in die Microsoft-Liste der besten Sicherheitsexperten aufgenommen.
Inform IT. Transform IT.
Informative Brancheneinblicke
Jetzt loslegen!
Unser Team bespricht gerne Ihre Anforderungen und unterstützt Sie aktiv beim Umgang mit Sicherheitslücken.