Schatten-IT
Kontrolle über Schatten-IT
„Schatten-IT“ bezeichnet beliebige IT-Assets, die Ihrem IT-Team nicht bekannt sind. Dazu zählen etwa Anwendungen, die von Einzelpersonen erworben wurden, Open-Source- und kostenlose Tools sowie EOL-Produkte, die noch immer verwendet werden. Wenn das Problem der Schatten-IT im Unternehmen ignoriert wird, können unkontrollierte Anwendungsausbreitung, Sicherheitslücken und unvorhergesehene Kosten die Folge sein. Flexera hilft Ihnen dabei, Schatten-IT aufzudecken und die Governance zu stärken, damit Sie keinem unnötigen Risiko ausgesetzt sind.
Empfohlene Produkte
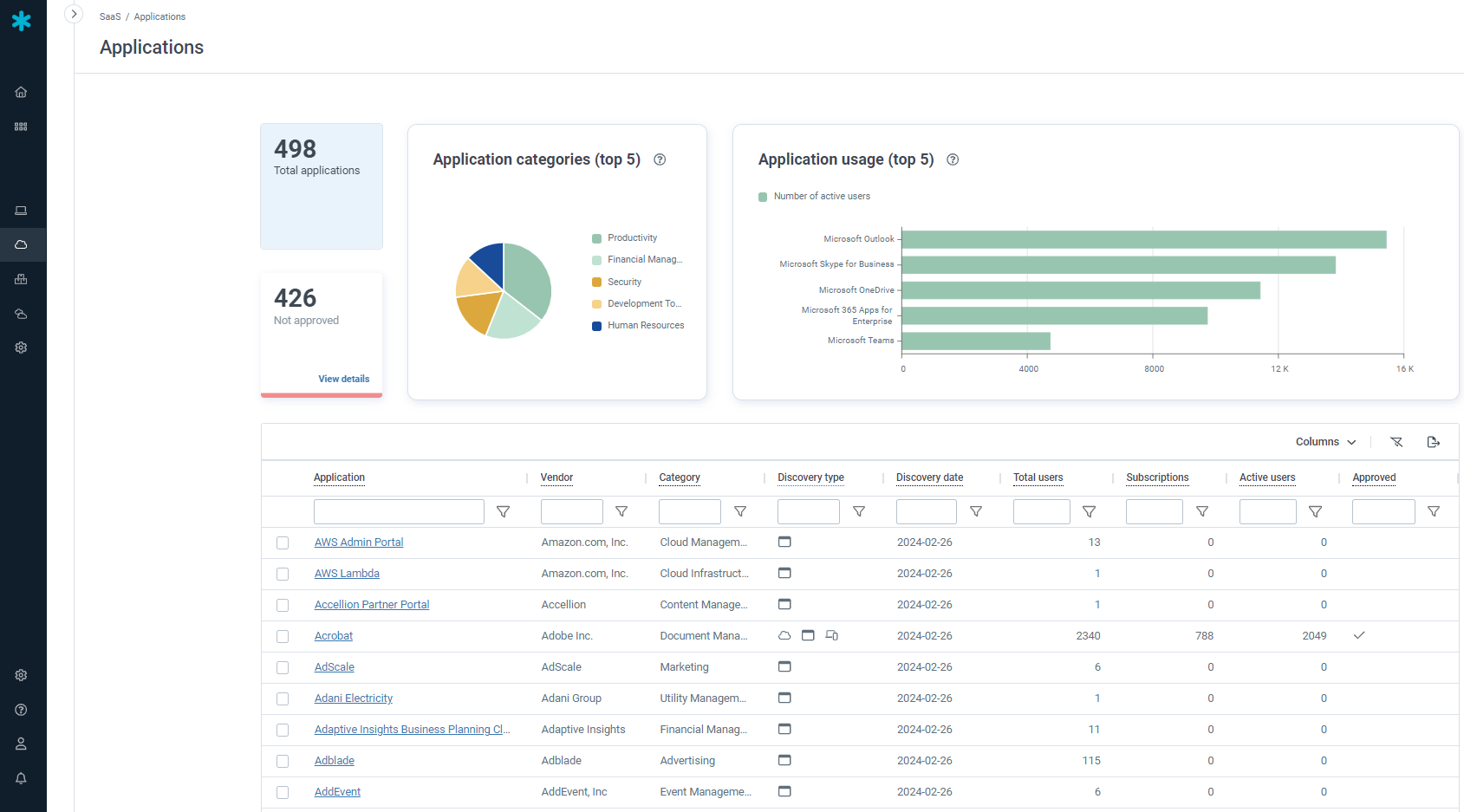
Aufdeckung von Schatten-IT zur Risiko- und Kostenkontrolle
Uncover shadow IT
Vollständige Transparenz zur Risikominimierung
Ohne umfassenden Überblick über SaaS-Anwendungen in Ihrem Unternehmen kann Schatten-IT unkontrolliert Überhand nehmen, sodass Ihr Unternehmen für Sicherheitsrisiken, unkontrollierte Anwendungsausbreitung und unnötige Kosten anfällig bleibt. Flexera verhilft Ihnen zur nötigen lückenlosen Transparenz über Ihre gesamte SaaS-Anwendungslandschaft – unabhängig davon, ob diese Anwendungen lizenziert, genehmigt oder autorisiert sind. Auf diese Weise können Sie Schatten-IT erkennen, Maßnahmen dagegen ergreifen und das Risiko senken, das von unbekannten SaaS-Ressourcen ausgeht.
Secure SaaS accounts
Risikominimierung bei Veränderungen im Unternehmen
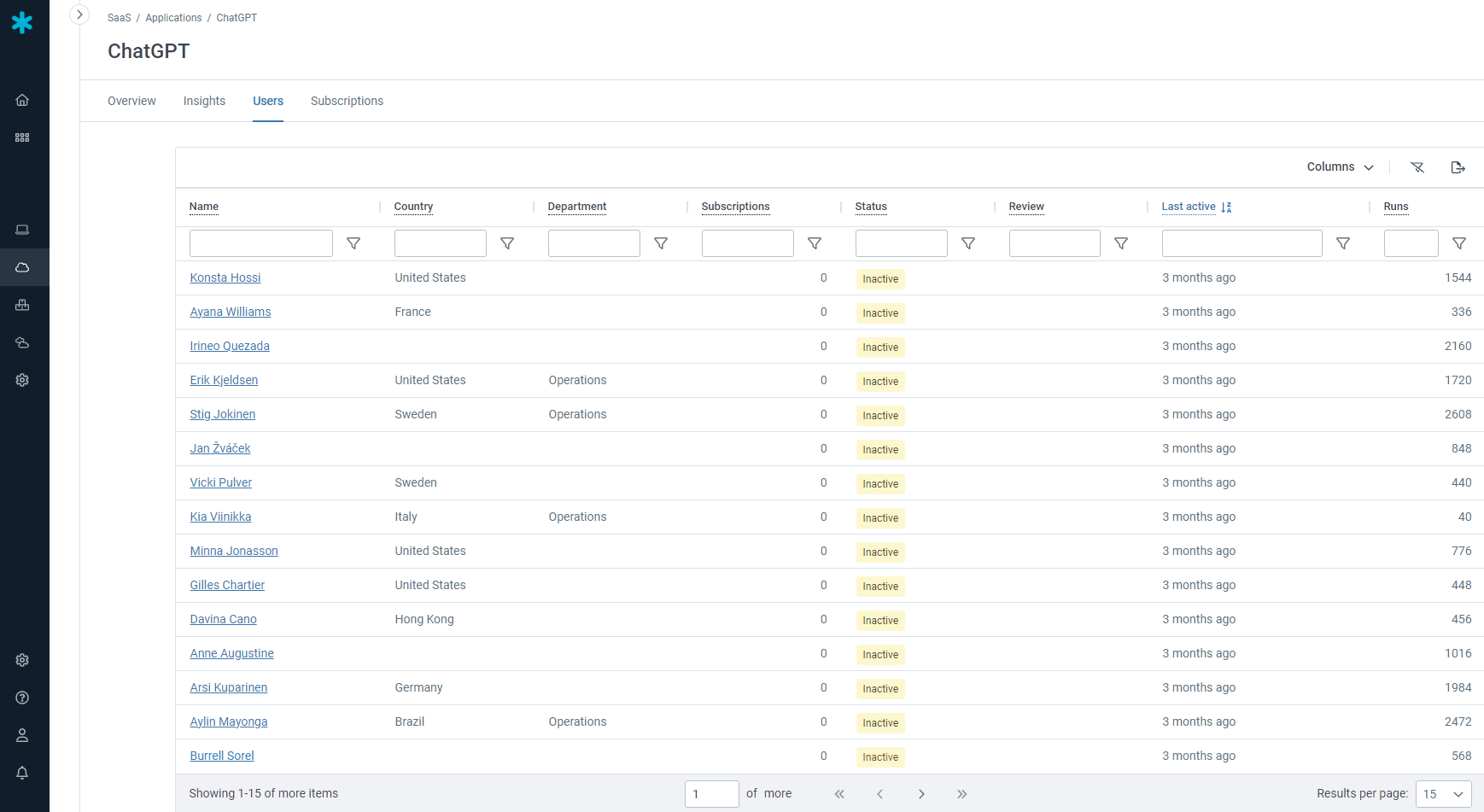
Durch Änderungen in der Zusammensetzung des Teams oder bei den Zuständigkeiten von Mitarbeitern kann sich Schatten-IT in den SaaS-Bestand einschleichen. Mithilfe von Flexera können Sie Nutzungsberechtigungen aktueller Mitarbeiter auf Governance-Richtlinien abstimmen, ehemaligen Beschäftigen den Zugriff automatisch entziehen und Ihre Unternehmensdaten gegen unbefugten Zugriff schützen.
Identify risk
Erkennung ungeprüfter SaaS-Anwendungen
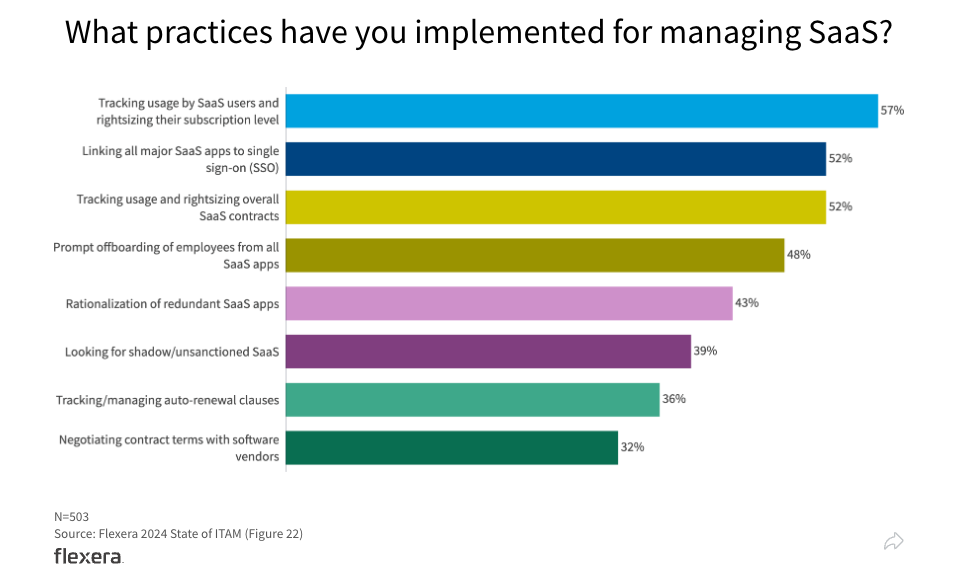
Allzu häufig umgehen Einzelpersonen oder Geschäftseinheiten bewährte Prozesse im Einkauf und nutzen kostenlose oder bezahlte SaaS-Anwendungen ohne eine vorherige Prüfung durch das IT-Sicherheitsteam. Dieses Vorgehen öffnet Tür und Tor für Sicherheitsrisiken und unerwartete Kosten. Verschiedene effektive Erkennungsmethoden, einschließlich Browsererweiterungen und Finanzaufzeichnungen, ermöglichen Ihnen die Erkennung solcher zusätzlichen Anwendungen, damit Sie das damit verbundene Risiko reduzieren und Maßnahmen gegen Schatten-IT ergreifen können. Gerade angesichts des dynamischen Softwaremarktes braucht es leistungsstarke und umfassende Erkennungsfunktionen, um Ihre SaaS-Anwendungen gegen Gefahren durch Schatten-IT abzusichern.
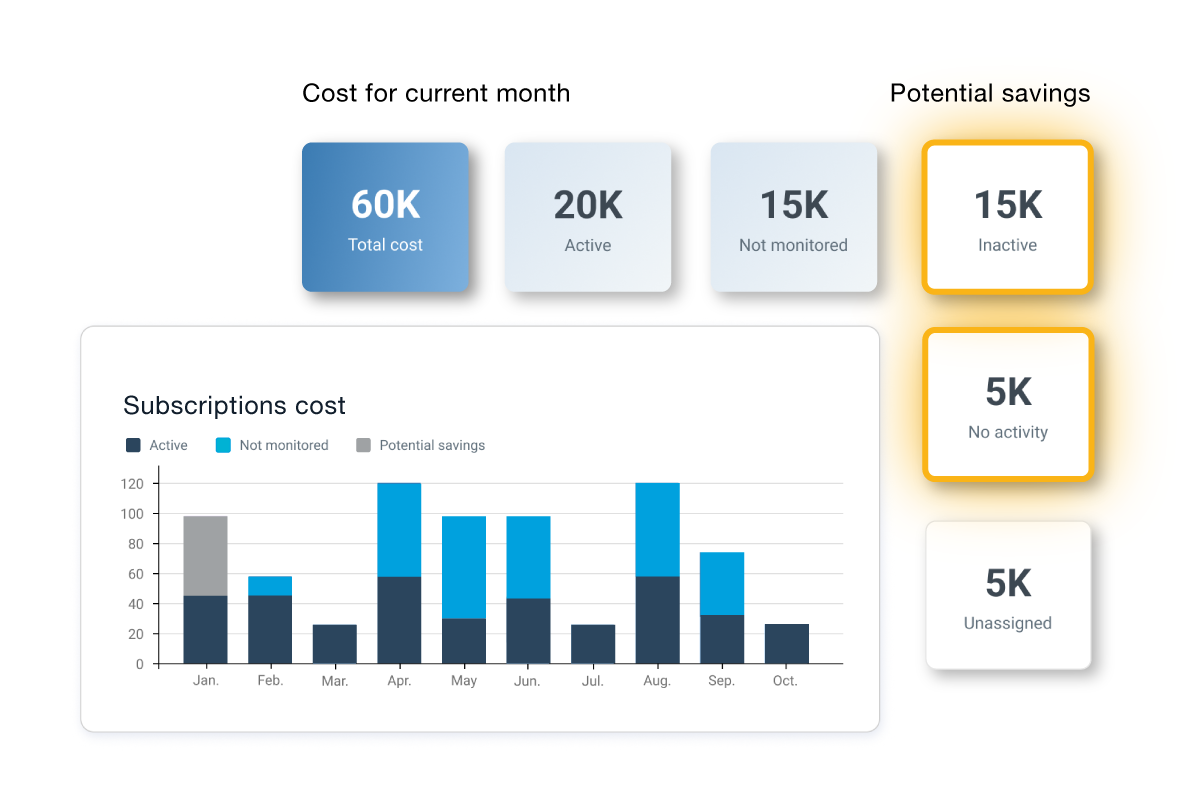
Shadow IT visibility
Erkennung von Schatten-IT
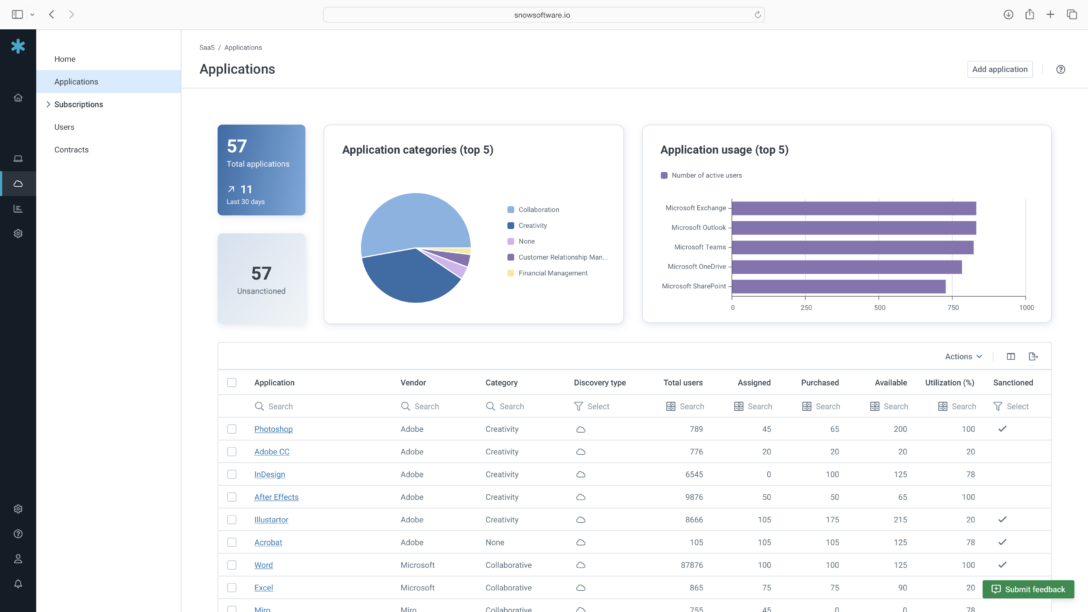
Um Schatten-IT zuverlässig aufzudecken, sind umfassende Erkennungsmaßnahmen erforderlich. Nur so kann Licht ins Dunkel der SaaS-Nutzung gebracht und ermittelt werden, an welcher Stelle Sicherheitsprüfungen in Ihrem Unternehmen umgangen wurden. Wir bei Flexera wissen, dass die effektive Identifizierung von Schatten-IT durch eine Kombination mehrerer Erkennungsmethoden erreicht werden kann, die vollständige Transparenz über genehmigte und nicht genehmigte SaaS-Nutzung gewährleistet. Nur so lassen sich Sicherheitsrisiken und unnötige Kosten reduzieren. Flexera bringt unterschiedliche Erkennungsmethoden zusammen, damit Sie genauestens darüber Bescheid wissen, welche Tools in den einzelnen Geschäftseinheiten zum Einsatz kommen, wer die Tools verwendet und auf welche Daten die Tools Zugriff haben.
Mithilfe der Lösungen von Snow machten wir 236 cloudbasierte Anwendungen ausfindig, von denen weder wir noch die Abteilungsleiter überhaupt wussten. Dazu kam auch noch unzulässige Gaming-Software, die wir bei Benutzern entdeckten. Dank Snow konnten wir uns Echtzeiteinblicke in Sicherheitsrisiken, Softwarenutzung und Assetbestand verschaffen, um dem Council die strategische Entscheidungsfindung zu erleichtern und so die zuverlässige Servicebereitstellung sicherzustellen.
Häufig gestellte Fragen (FAQs)
Als „Schatten-IT“ werden alle IT-Assets bezeichnet, von denen Ihr Team keine Kenntnis besitzt. Der Technologieeinkauf hat durch SaaS-Hersteller, die sich über produktgesteuerte Wachstumsinitiativen an Abteilungseinkäufer (CMO, CRO, CTO) und Endbenutzer wenden, eine immer stärkere Dezentralisierung erfahren. Im weiteren Sinne kann Schatten-IT Folgendes umfassen:
• Anwendungen, die von einzelnen Mitarbeitern erworben wurden
• Unternehmensanwendungen, die von einer Abteilung/einem Geschäftsbereich gekauft wurden
• Open-Source- oder kostenlose Anwendungen
• Anwendungen, die in der Vergangenheit verboten wurden, aber weiterhin von Mitarbeitern verwendet werden
• Anwendungen, die ihr Produktlebensende (EOL) erreicht haben, aber nach wie genutzt werden
Es gibt diverse Möglichkeiten zum Aufdecken von Schatten-IT.
• Nutzungsmessung: Anhand der Nutzungsmessung lässt sich schnell feststellen, welche Anwendungen von Mitarbeitern tatsächlich genutzt werden. Dadurch wissen Sie nicht nur, wann die letzte Anmeldung durch welchen Benutzer erfolgt ist, sondern können auch in Erfahrung bringen, wie häufig eine Anwendung in einem bestimmten Zeitraum wie lange genutzt wurde, um auf diese Weise häufige und gelegentliche Nutzer einer Anwendung zu erkennen.
• Cloud Access Security Broker (CASB): CASBs können nicht nur die Nutzung von Cloudanwendungen erkennen, sondern auch Nutzungsanomalien (und somit potenzielle Bedrohungen wie Ransomware) aufdecken und Richtlinien zur gezielten Einschränkung des Zugriffs durchsetzen.
• Low-Tech: Finden Sie heraus, welche Anwendungen in den einzelnen Abteilungen unverzichtbar sind. In der Regel können Betriebsteams genauere Angaben zu den wichtigsten Anwendungen machen, die für den Erfolg ihrer Teams entscheidend sind.
Mit angemessener Transparenz und entsprechenden Richtlinien ist die Schatten-IT gut regulierbar. Der Einkauf kann anhand von SSO-Plattformen und Selfservice-Funktionen sicherstellen, dass Mitarbeiter ohne großen Aufwand das erhalten, was sie benötigen. Ein nach Kategorie und Abteilung sortiertes Verzeichnis des Anwendungsbestands kann bei der Gegenprüfung von genehmigten Anwendungen helfen, die sich bereits in Gebrauch befinden.
Inform IT. Transform IT.
Informative Brancheneinblicke
Webinar
Innovatives SaaS Discovery
Erfahren Sie, wie Sie SaaS-Applikationen überwachen, Sicherheits- und Compliance-Richtlinien einhalten und Kosten kontrollieren können.
Englisches Webinar
Flexera 2024 State of ITAM Report webinar
The Flexera 2024 State of ITAM Report highlights the pivotal role of cross-team collaboration for ITAM teams this year. Don’t miss the opportunity to benchmark your enterprise against peers and discover tips to set your organization up for success.
Bericht
Der Flexera 2025 State of the Cloud Report
Wie werden GenAI, steigende Cloud-Kosten, Sicherheit und Nachhaltigkeit Ihre Cloud-Strategien im Jahr 2025 beeinflussen?
Bericht
State of ITAM Report 2024 von Flexera
Der State of ITAM Report 2024 von Flexera beleuchtet wie wichtig ein ordnungsgemäßes IT- Asset-Management ist, die Herausforderungen, die damit einhergehen, sowie Lösungsansätze dieser. Mehr dazu im aktuellen Report.
Leitfaden
Kurzleitfaden: Zukunftsfähige Technology Intelligence im Jahr 2025
Entdecken Sie die Schlüsselfaktoren für echte Technology Intelligence.
Leitfaden
Kurzleitfaden: Zukunftfähiges SaaS im Jahr 2025
Entdecken Sie die wichtigsten Erfolgsfaktoren von SaaS in Ihrem Unternehmen.
Jetzt loslegen!
Unser Team bespricht gerne Ihre Anforderungen und erklärt im Rahmen einer Demo, wie Sie Schatten-IT erkennen und Risiken minimieren.