Software Vulnerability Management
Alles im Blick
Die meisten Sicherheits-Exploits betreffen Schwachstellen, die seit über einem Jahr bekannt sind. Viele Unternehmen verfügen jedoch nicht über ausreichend Ressourcen, um diese zu beheben. Mit Flexera optimieren Sie die Erkennung und Behebung von Schwachstellen und priorisieren Ihre nächsten Schritte basierend auf vertrauenswürdigen Daten von Secunia Research.
Empfohlene Produkte
Besser gewappnet gegen Cyberangriffe
Stay secure
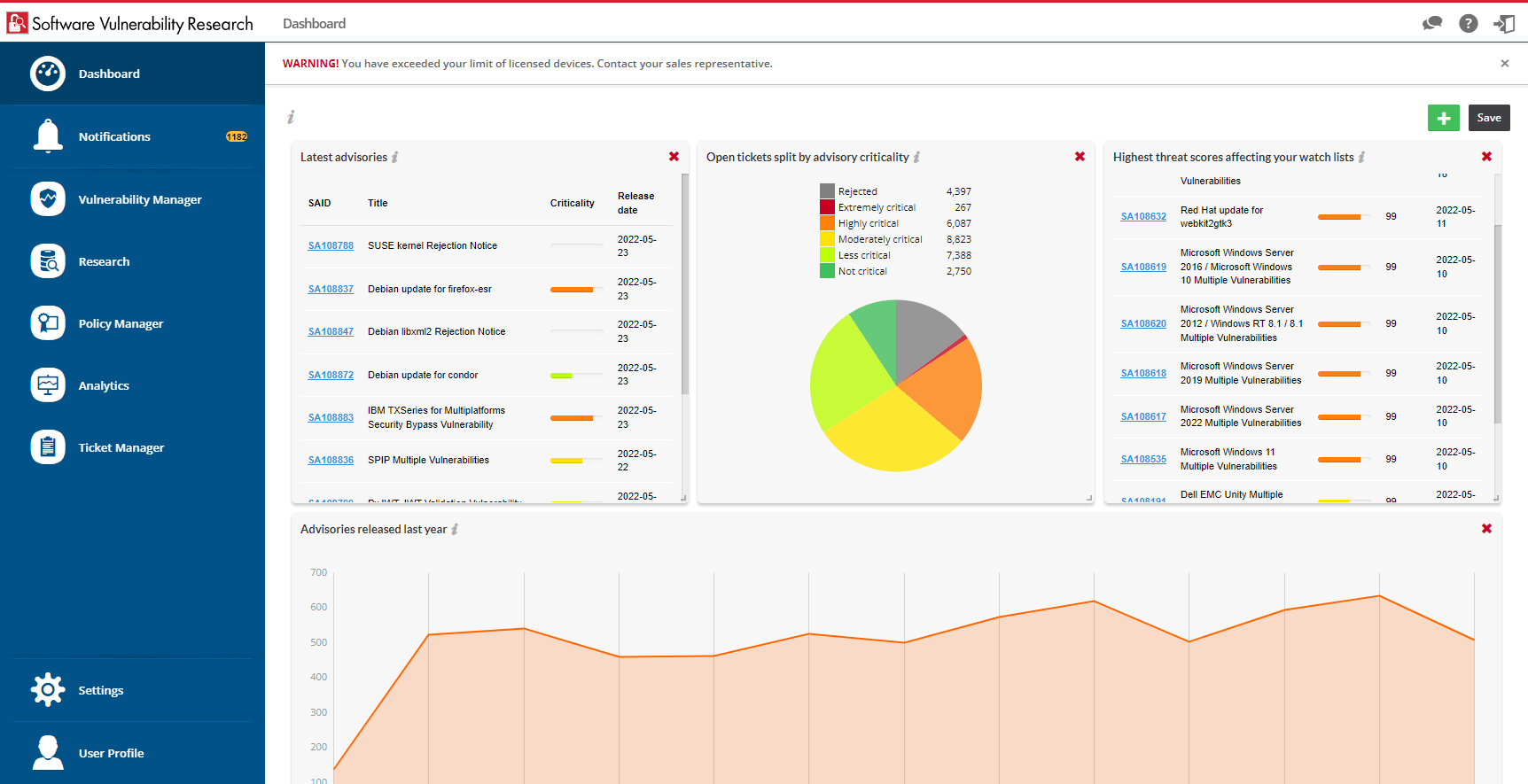
Lückenloses Management von Softwareschwachstellen
Zur effektiven Risikominimierung benötigen Sie Prozesse, die Richtlinien mit Maßnahmen für das Schwachstellen- und Patchmanagement Ihrer Software verknüpfen. Flexera vermittelt Ihnen ein klares Bild Ihrer Umgebung sowie ein umfassendes Verständnis der Verwaltung von Schwachstellen und Patches, um Sie bei der Behebung kritischer Sicherheitsprobleme zu unterstützen.
Collaborate effectively
Vollständige Transparenz für Software
ITAM-Experten können Sicherheitsteams in die Lage versetzen, im Fall von Sicherheitslücken im Softwarebestand den entsprechenden Titel oder die Version schnell ausfindig zu machen. Das erleichtert die Durchführung von Schwachstellenprüfungen vor der Anwendungsbereitstellung und gewährleistet, dass Sie Ihre Umgebung keinen unnötigen Risiken aussetzen. Außerdem werden Qualitätsinitiativen gestärkt und Softwarekataloge bereinigt.
Make prioritization a priority
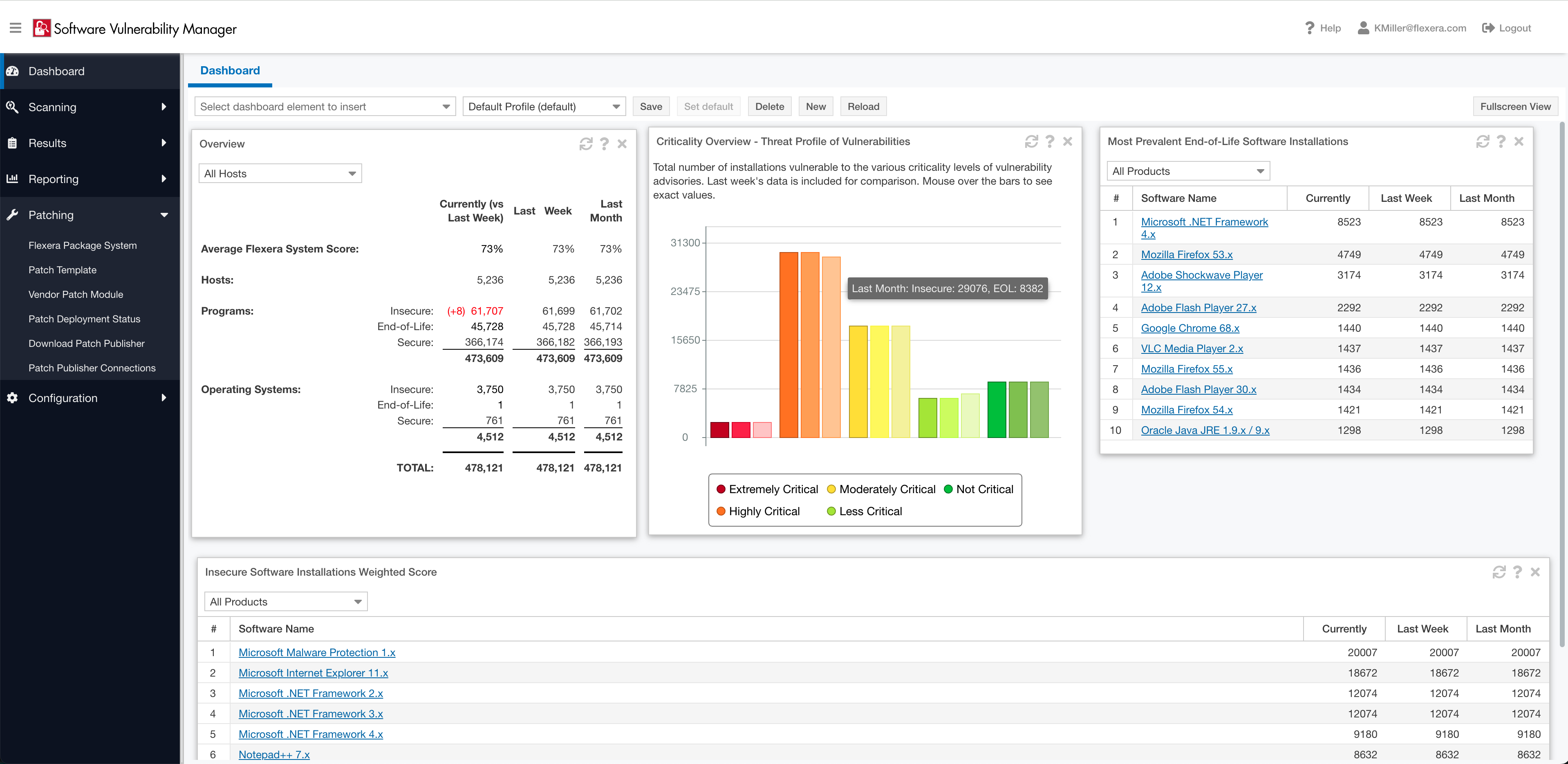
Verknüpfung von Bewertung und Patching zur effizienten Problembehebung
Erkennen und verfolgen Sie mit Flexera mehr Anwendungen auf Windows-, Mac- und Linux-Plattformen als mit jedem anderen Hersteller. Befolgen Sie die Sicherheitsempfehlungen, sogenannte Advisories, von Secunia Research, um Ihren Priorisierungsprozesses zu vereinfachen. Sie erhalten Informationen zu Schweregrad, Bedrohungsbewertung, Auswirkungen und Angriffsvektoren sowie weitere Angaben, die Sie bei der Erarbeitung geeigneter Lösungen für Ihr Unternehmen unterstützen.
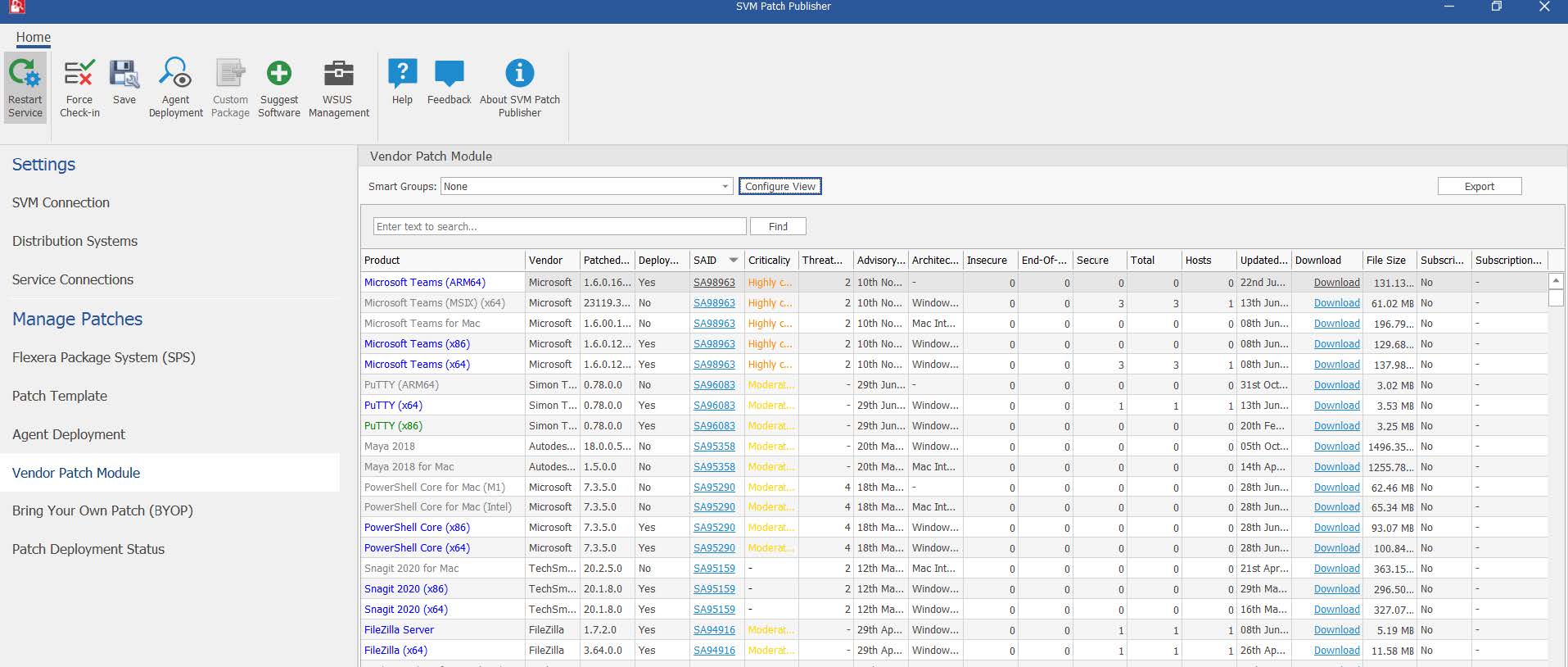
Intelligent automation
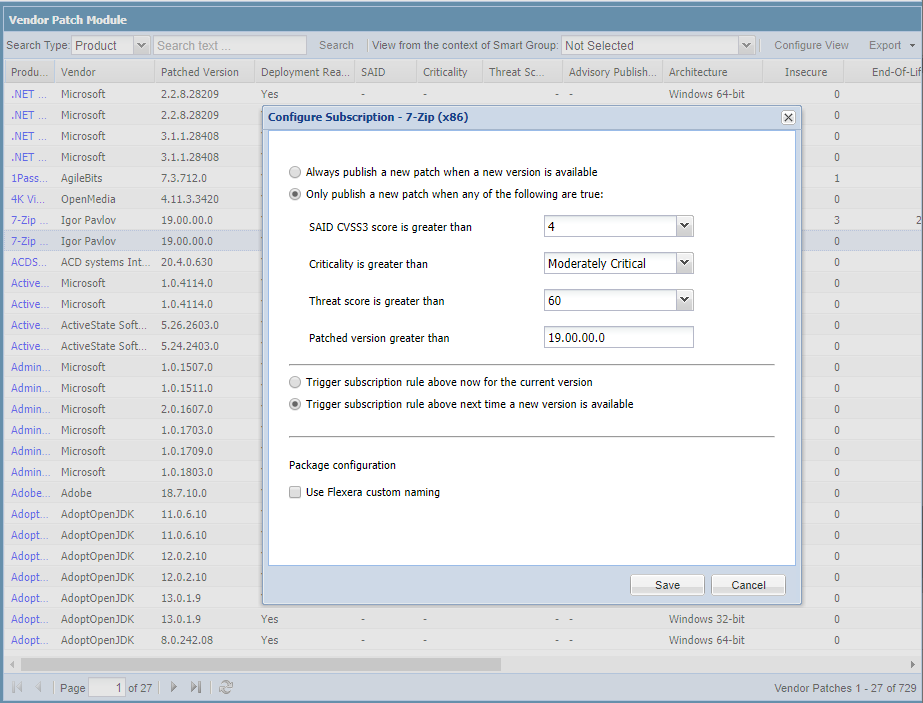
Effizienter Umgang mit Zeit und Ressourcen
Beschleunigen Sie die Problembehebung, und optimieren Sie das regelmäßige Patchen durch Automatisierung. Lassen Sie Routineaufgaben automatisch ablaufen, und konzentrieren Sie sich stattdessen auf komplexere Anwendungen. Wählen Sie gezielt Anwendungen zur Automatisierung aus, und legen Sie Bedingungen fest, sodass nur die Versionen mit dem größten Potenzial installiert werden.
Improve risk mitigation
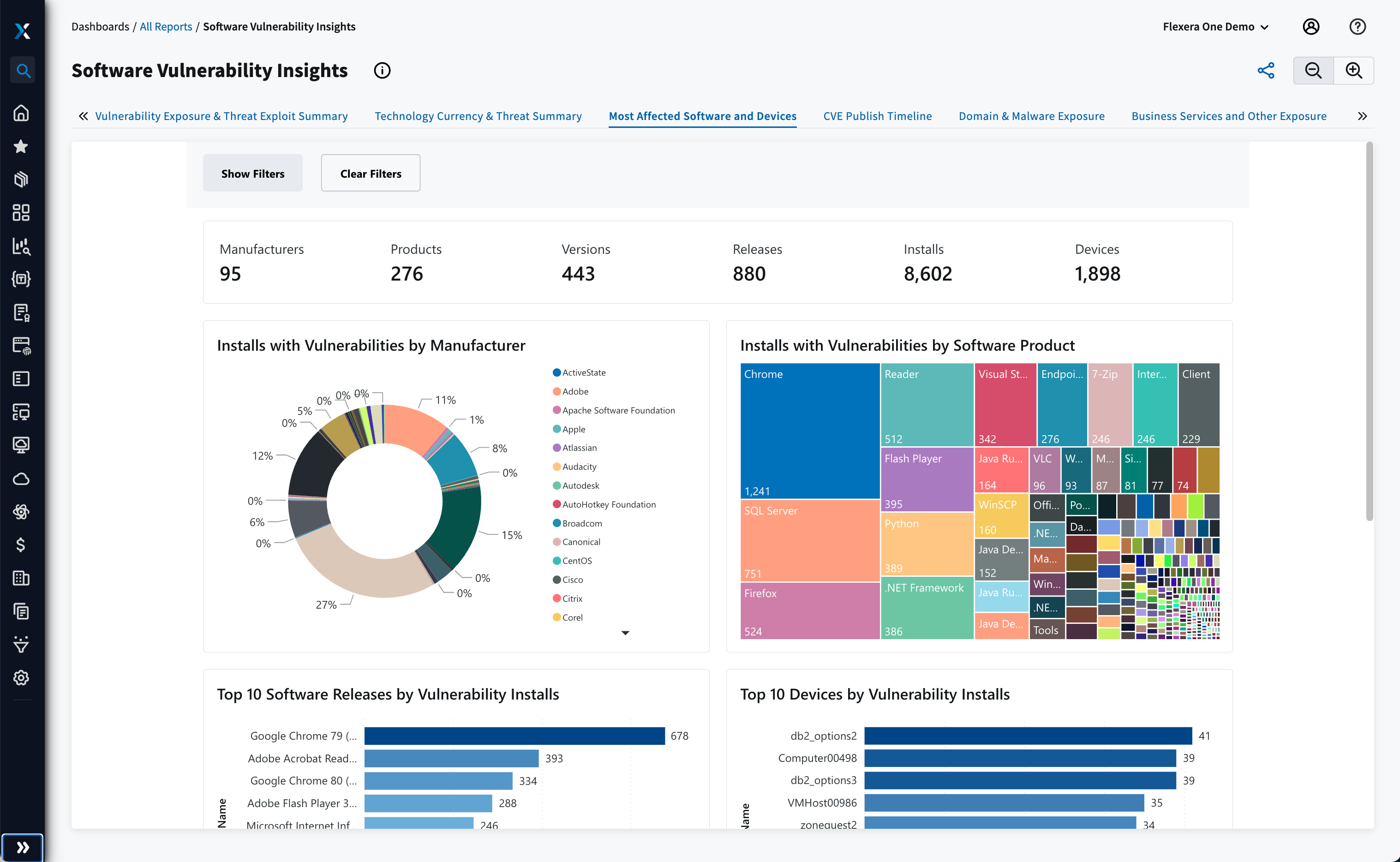
Intelligente Priorisierung mit Bedrohungsdaten
Nur 6 bis 8 % der Schwachstellen werden ausgenutzt. Um Schaden von Ihrem Unternehmen abzuwenden, ist rechtzeitiges Patchen erforderlich. Mit umfassenden Einblicken können Sie Sicherheitsprobleme effektiv priorisieren und anhand von Bedrohungsdaten die anfälligsten Schwachstellen bestimmen. Die neue Metrik zur Bewertung von Bedrohungen von Flexera ordnet die wertvollen Erkenntnisse Ihren nicht gepatchten Produkten zu, um sicherzustellen, dass Sie sich den Patches widmen, die mit dem höchsten Risiko der Ausnutzung verbunden sind.
More than 18,000 vulnerability emerge every year
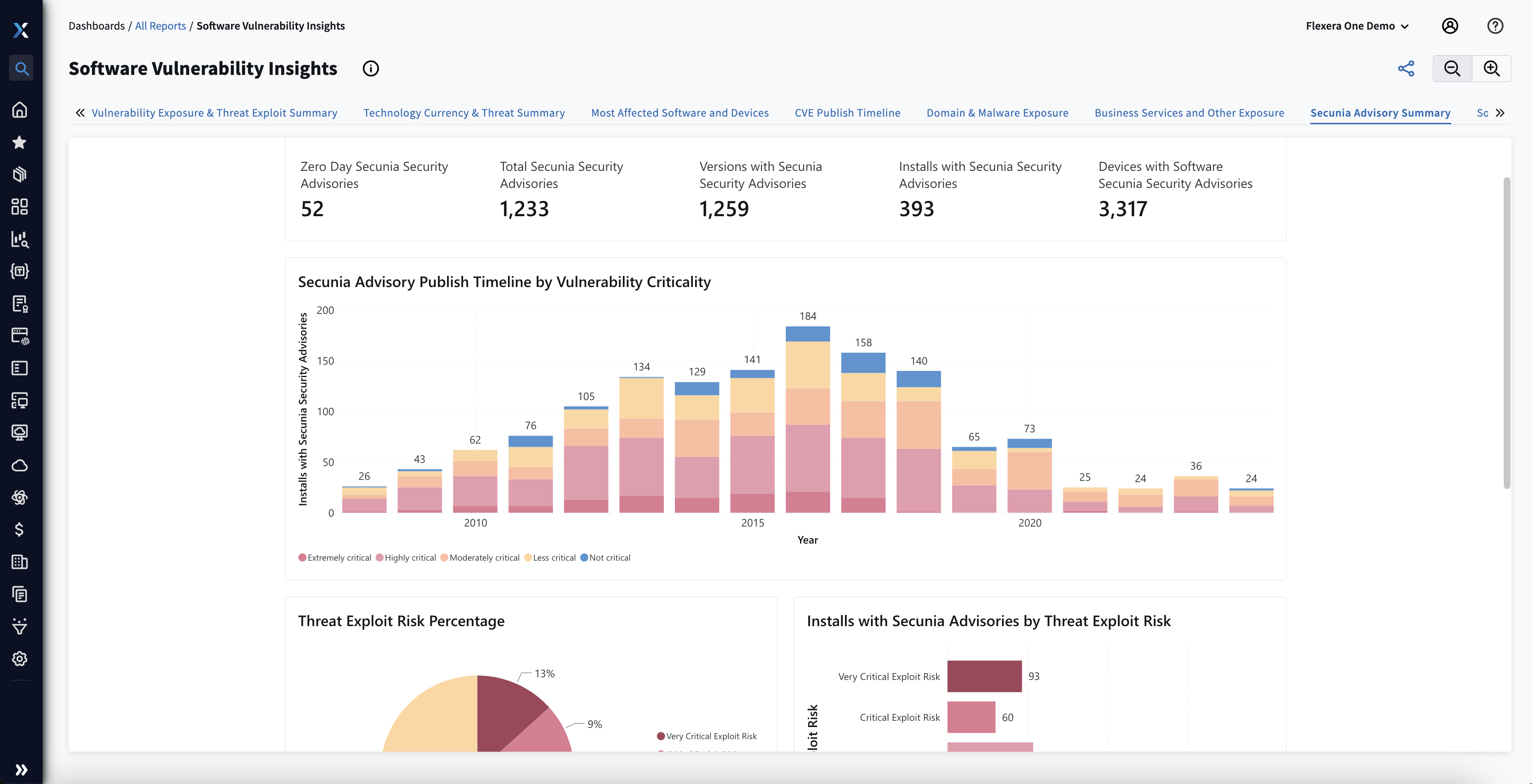
Sharpen vulnerability remediation
Entscheidende Daten im entscheidenden Moment
Ergreifen Sie bei Sicherheitsproblemen effektive Behebungsmaßnahmen mithilfe der vom Secunia Research-Team von Flexera bereitgestellten Advisories, die alle Schwachstellen im Zusammenhang mit einer bestimmten Produktversion abdecken. Patchen Sie besonders gefährdete Schwachstellen mithilfe eines fortlaufend aktualisierten Bewertungssystems. Dank Flexera kennen Sie potenzielle Auswirkungen, Angriffsvektor und Quelle und können auf noch mehr Details zugreifen, um den Kontext in Ihrer Umgebung zu verstehen.
Flexera ist zu einem grundlegenden Bestandteil unseres Patchmanagementsystems geworden. Nie hatten wir einen besseren Überblick als jetzt. Der komplexe, schwierige und zeitaufwändige Prozess ist jetzt strukturierter, priorisiert und zielgerichtet. Damit sind wir besser aufgestellt als je zuvor.
Häufig gestellte Fragen (FAQs)
Bei einer Softwareschwachstelle handelt es sich um einen strukturellen oder konzeptionellen Mangel in einer Softwareanwendung, der von Angreifern ausgenutzt werden kann, um die Sicherheit, Funktionsfähigkeit oder Integrität des Systems, des Netzwerks oder der Daten zu gefährden, mit denen diese Software interagiert. Weitere Informationen finden Sie hier in unserem Glossar.
Bei der Umsetzung einer umfassenden Strategie, mit der Softwareschwachstellen minimiert und Ihr Unternehmen geschützt werden soll, können diverse Probleme auftreten. Zu den gängigen Herausforderungen zählen z. B. eingeschränkte Ressourcen, Systemkomplexität, Abhängigkeiten von Drittanbietern, Altsysteme, Zeitvorgaben, Fachkräftemangel und die Einhaltung gesetzlicher Vorschriften. Klicken Sie hier, um mehr zu erfahren.
Ein ausgereifter Plan für das Management von Softwareschwachstellen stärkt Ihre gesamte Cybersicherheit und reduziert so das Risiko von Datenschutzverletzungen, unbefugtem Zugriff und Serviceunterbrechungen. Durch die Vermeidung eines möglichen Schadens wahrt Ihr Unternehmen seinen Ruf, das Vertrauen der Kunden und die Compliance mit gesetzlichen Vorgaben.
Wenn Sie wissen möchten, wie Sie Ihr Unternehmen vor Softwareschwachstellen schützen können, nehmen Sie an unserer nächsten Roundtable-Session teil.
Inform IT. Transform IT.
Informative Brancheneinblicke
Webinar
Innovatives SaaS Discovery
Erfahren Sie, wie Sie SaaS-Applikationen überwachen, Sicherheits- und Compliance-Richtlinien einhalten und Kosten kontrollieren können.
Englisches Webinar
Flexera 2024 State of ITAM Report webinar
The Flexera 2024 State of ITAM Report highlights the pivotal role of cross-team collaboration for ITAM teams this year. Don’t miss the opportunity to benchmark your enterprise against peers and discover tips to set your organization up for success.
Bericht
Der Flexera 2025 State of the Cloud Report
Wie werden GenAI, steigende Cloud-Kosten, Sicherheit und Nachhaltigkeit Ihre Cloud-Strategien im Jahr 2025 beeinflussen?
Bericht
State of ITAM Report 2024 von Flexera
Der State of ITAM Report 2024 von Flexera beleuchtet wie wichtig ein ordnungsgemäßes IT- Asset-Management ist, die Herausforderungen, die damit einhergehen, sowie Lösungsansätze dieser. Mehr dazu im aktuellen Report.
Leitfaden
Kurzleitfaden: Zukunftsfähige Technology Intelligence im Jahr 2025
Entdecken Sie die Schlüsselfaktoren für echte Technology Intelligence.
Leitfaden
Kurzleitfaden: Zukunftfähiges SaaS im Jahr 2025
Entdecken Sie die wichtigsten Erfolgsfaktoren von SaaS in Ihrem Unternehmen.
Effektive Priorisierung der Schwachstellenbehebung
Wir sind für Sie da, wenn es darum geht, Ihnen mit unserem Know-how beim Management von Softwareschwachstellen zu helfen.